This free Cloudflare hack protects against WordPress brute force attacks

If you read this blog, you’ll know that we take website security very seriously. And we always recommend using the Cloudflare service as one of the tools in your security toolbox. In this post we will share a simple Cloudflare hack that blocks many of the WordPress brute-force attacks your site experiences every day.
Why is WordPress security important?
Insecure web sites are a major problem on the internet. For site owners, defacement or loss of functionality can cause serious harm to their reputation as a trusted online resource. Lost revenue can also be a big problem.
And if an intruder gains access to the site backend, the database, and/or the hosting account, the risks may escalate. Customer/member data is at risk of unauthorized exposure. And the server may be added to a bot network and used in illegal activity online.
With so much at stake, security is one of the main responsibilities for anyone maintaining a WordPress web site.
WordPress brute force attacks are common
Like all web sites, automated attacks are very common. Large networks of computers run scripts that scan the internet looking for common vulnerabilities.
For WordPress, one of the most common vulnerabilities that these scripts try to exploit are weak user passwords. To do this, the attacking script finds a domain and tests if the site has an accessible WordPress login form at one of these two well-known URLs:
/wp-admin/wp-login.php
When a WordPress login form is found, the script will then try to log in with a series of common username and password combinations. Because these automated attacks only work when a large number of usernames/passwords are tested, they are known as “brute-force” attacks.
Luckily, you can use the free WordPress security hack (below) with the Cloudflare service to stop these attacks cold.
What is Cloudflare?
Technically, Cloudflare is a “domain name server proxy”. That’s a fancy way of saying that it acts like a traffic cop for your website. If your site is using Cloudflare, then each visitor or malicious script gets scrutinized when it tries to access your website. Cloudflare examines the URL or “request” and tries to determine if there is anything suspicious.
For example, long URLs with complicated parameters can sometimes be used to exploit a vulnerability in a plugin or theme. Cloudflare has a large database of these patterns. If it detects one of these patterns in a request, it can block the user or script, or present it with a challenge to make sure it is a human.
Once a challenge is completed successfully, or when requests look legitimate, Cloudflare then directs the request to your webserver where the appropriate content is displayed.
Importantly, this process happens before any traffic hits your actual web server. Unlike a security plugin installed in your WordPress backend, Cloudflare takes the load for every request sent to your domain.
Cloudflare has many types of tricks for keeping your site secure, including for sites using the free plan. This is why we recommend it for all WordPress sites.
Easily block WordPress brute force attacks with Cloudflare
Using strong username and password combinations is the most important way to prevent a brute force attack from allowing unauthorized access to your website.
However, prolonged brute force attempts can negatively impact the performance of your server causing long page load times. In extreme cases, it can cause your site and server to go offline.
If you review the official brute force guidance from WordPress, you’ll see that preventing scripts from attempting a WordPress brute force attack is not trivial. It requires good knowledge of servers and server configurations.
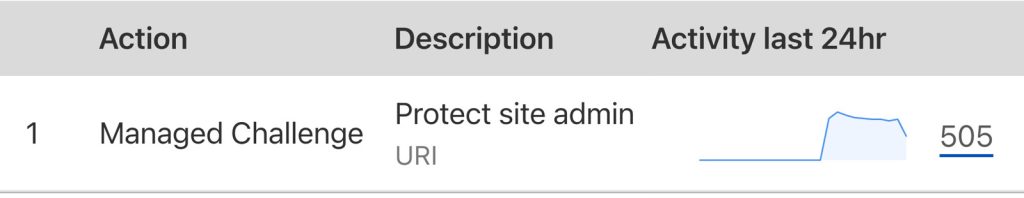
Thankfully, you can configure the Cloudflare web application firewall or “WAF” to effectively block many brute force attacks. For example, on a low-traffic brochure site the Cloudflare WAF blocked over 500 suspicious requests in just a few hours.
Adding the WordPress security hack to Cloudflare in 60 seconds
Configuring Cloudflare to block most brute force attacks on your admin area can be completed in a few clicks, and works on the free version of Cloudflare.
- Log into your Cloudflare account.
- Select your site from the dashboard.
- In the menu at the left, select
Security > WAF. - Click the
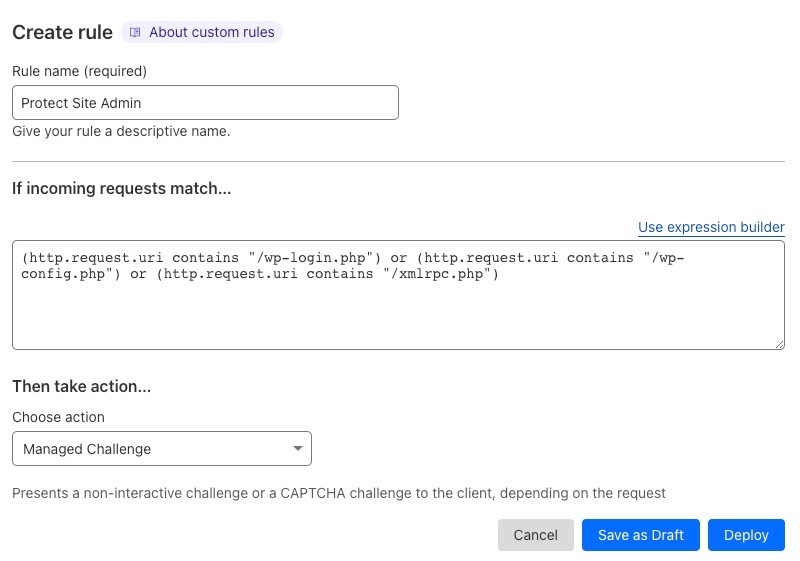
Create firewall rulebutton. - In the rule editor:
- Enter a
Rule name. - Click the
Edit expressionlink and paste the following:(http.request.uri contains "/wp-login.php") or (http.request.uri contains "/wp-config.php") or (http.request.uri contains "/xmlrpc.php") - On the
Choose an actiondropdown, selectManaged Challenge. - Click the
Deploybutton.
- Enter a


3 Comments
Atreus · January 28, 2026 at 1:27 AM
Great explanation — practical and easy to apply.
Erick · December 17, 2025 at 1:52 AM
Nice article — learned a couple of useful points I didn’t know before.
Demian · September 3, 2024 at 10:45 AM
Thanks for this, it was very helpful